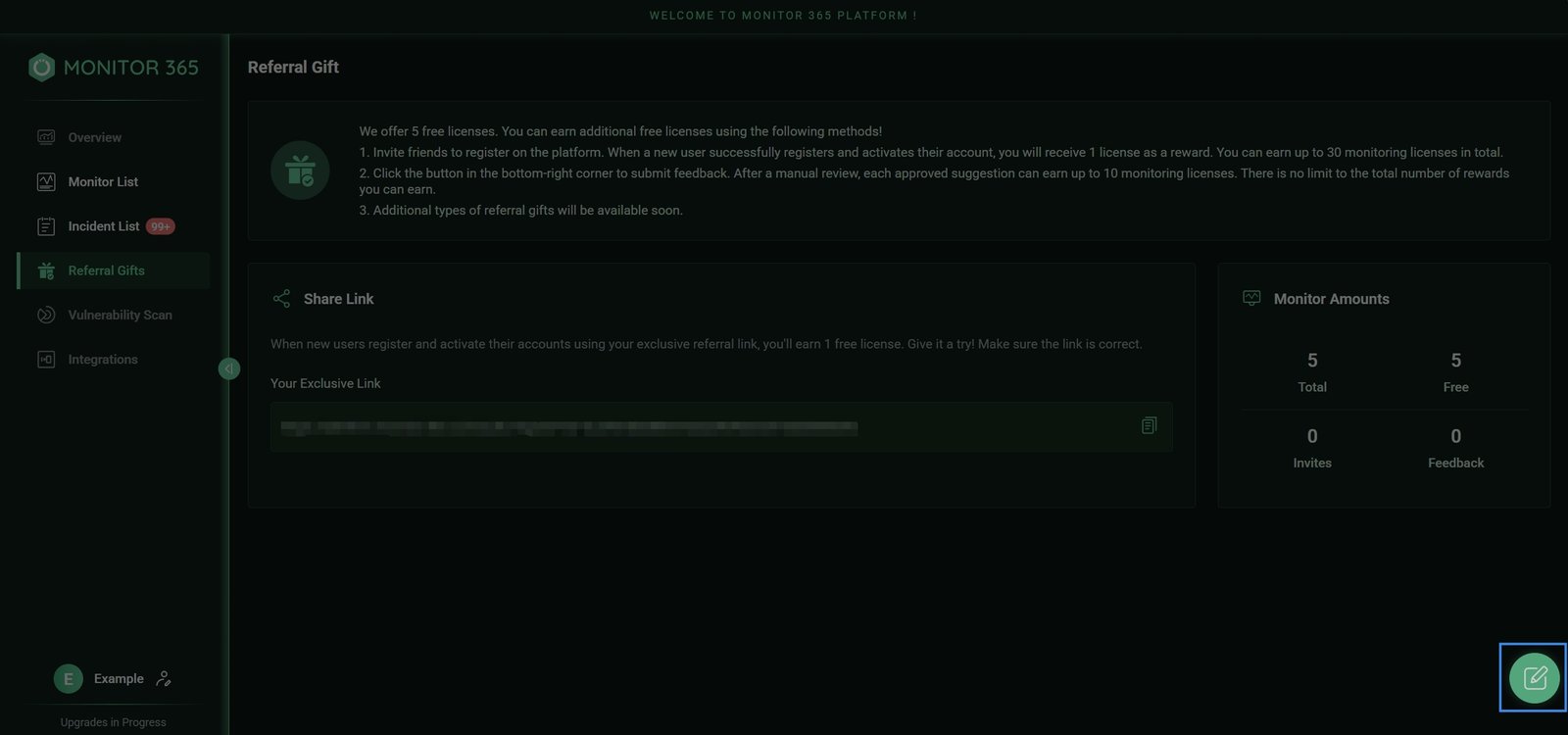
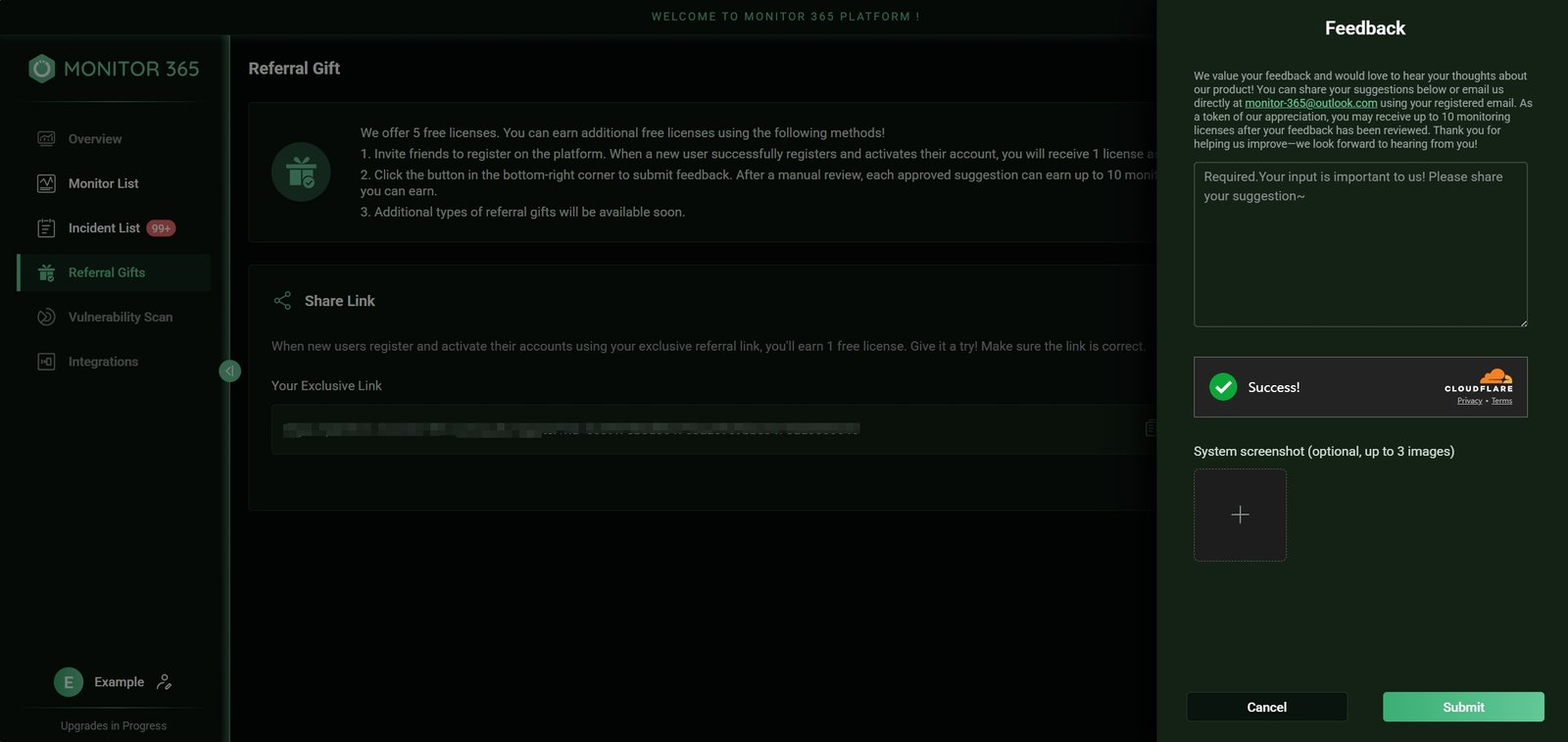
As a startup team, your suggestions and feedback mean the world to us! We eagerly look forward to hearing from you to help improve our product. You can easily submit through:
In-platform feedback
After logging in, click the “Feedback” button in the bottom-right corner of any page to access the feedback form. Describe your specific requests, and we’ll promptly follow up upon submission.
Email us
Reach out anytime at monitor-365@outlook.com. Whether it’s a desired new feature, experience optimization, or any ideas while using the product, feel free to share.
💡Tip
Feedback submitted through the official in-platform channel will earn you free licenses upon review and approval!